
????????????????????????????????????????????????????????????????????????????????????????????????????
??Crypto
一、[签到]古典大杂烩
附件信息:
??????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????????
很明显可以看出来是base100,密码工具箱一把梭:

SICTF{fe853b49-8730-462e-86f5-fc8e9789f077}
二、Radio
附件信息
查看代码
from Crypto.Util.number import *from flag import flagm = bytes_to_long(flag)p = getPrime(1024)q = getPrime(1024)n1 = p * qp = getPrime(1024)q = getPrime(1024)n2 = p * qp = getPrime(1024)q = getPrime(1024)n3 = p * qe = 17c1 = pow(m,e,n1)c2 = pow(m,e,n2)c3 = pow(m,e,n3)print("n1 =",n1)print("n2 =",n2)print("n3 =",n3)print("c1 =",c1)print("c2 =",c2)print("c3 =",c3)'''n1 = 14628911682936716611458501697007036859460044243525290515096052103585430459755335375005202100114469571371360084664887335211277585652711111523095037589648375630146039444071400098427638768750755153219974194380355807078158427824557754939604018020265955042573660474772006646525311705184431094905718137297923127124517126579859336516891364853724635334011666814712424599592662398013241607855160919361308195967978220182785816761656927836373944699635667244275310680450562446433724968942835275279255823144471582249379035668825437133182865600026935116686574740844588839352146024513673500770611055698030333734066230166111140083923 n2 = 16756694748293603983474688536179571665757862433174984877308316444468003022266277794769268134195205510197588585566270416339902269736376811449830775290335951504698137924773942880807921752691668522662285163130340474205633998154849689387759453003838730282756734975490180702422176361373516245372635401939755527017589503572550811648345570775428936487145892225736625411540461653083957762795820510109891180906709827194217045059033312564525916136573856999724346161896146703174418039344166251503310869772735585554127509732135494936119159784702673291794381095696332128950979288440758815310482211285712819274848744478643590996499 n3 = 12023158079717019193506148537498877243668782424904061914991928068483879707115315968983829360560644394409575645736275352836086080024994045582242629571839276759393418303915955798990522990081795218822313146157773272844272865701134880180795342597049645358985187689813369428579614193015028249821853347208001645148169449968882591709833452960545988520048722323580338213590245476892223967673180144525106292453573842357322398199104132677638909964034937501684668442732786408572501007756270725934445316827054687741612177409932320532825182104820899546084015733164816993674100635828218335112393003462442685677115798304835391938681 c1 = 786426913645332991929803636719878643130489430090701482974255190570111407517277263761161970232982615374753982050075781017755721714929721429185828101898786972242994012456972241276851428750970754773002966788642795040933520662931514953660571657013642671173456750800960592586345219252277575624120271330470724245201080094330964145796872211627254805407394764183615099525852600855622089361965086460279057625205099471122036599934609091062009161119885692567925924978687256063116915630947838112126347748759078024890458539541208153526564434483654508834147071166870006117573542198238493913144419569943131642262575848786399020602 c2 = 14269311999815379511888097227418748728398011595172649708273598243317106830139061994801598925448165045032084910971094414749744701731066555194159863759072739031915833091715422787808666326235589236328864675164322734119047182014621724868200908222400504845559290620275973427127376594365043386362821355037781568524903149101953873768462097165128186788759111090267131443645126715520994688945363059795513931799317608292977574376954729552861360597103229877031117089231816770880909815561950691603994439997197261395452797893557057320175747162837857668062550646101714062365530246698404923128445182100334335447738834779014705114350 c3 = 3204718091370324153305164801961074660508922478706979436653573192321723216725523523538914956544950802616295043619768261075799875855502834749045520466140056621489305006966280527055668378303630674311102581232313032585389907028715671091914904062961720585667564982641321454541632782484415075257140508738041786400512095949826279576159569786734978545737717138115729502475357594151593143140355121154223614868465202149338507796306863351134218879326031985027900678671697876083351974546516576983143592764763925335805465720148057651958521255276602933604064541840892578409973858867533575728482926007556060584654853884046046420855 '''
广播攻击+中国剩余定理
exp:
import gmpy2import libnum# n1,n2,n3......两两互质n1 = 14628911682936716611458501697007036859460044243525290515096052103585430459755335375005202100114469571371360084664887335211277585652711111523095037589648375630146039444071400098427638768750755153219974194380355807078158427824557754939604018020265955042573660474772006646525311705184431094905718137297923127124517126579859336516891364853724635334011666814712424599592662398013241607855160919361308195967978220182785816761656927836373944699635667244275310680450562446433724968942835275279255823144471582249379035668825437133182865600026935116686574740844588839352146024513673500770611055698030333734066230166111140083923 n2 = 16756694748293603983474688536179571665757862433174984877308316444468003022266277794769268134195205510197588585566270416339902269736376811449830775290335951504698137924773942880807921752691668522662285163130340474205633998154849689387759453003838730282756734975490180702422176361373516245372635401939755527017589503572550811648345570775428936487145892225736625411540461653083957762795820510109891180906709827194217045059033312564525916136573856999724346161896146703174418039344166251503310869772735585554127509732135494936119159784702673291794381095696332128950979288440758815310482211285712819274848744478643590996499 n3 = 12023158079717019193506148537498877243668782424904061914991928068483879707115315968983829360560644394409575645736275352836086080024994045582242629571839276759393418303915955798990522990081795218822313146157773272844272865701134880180795342597049645358985187689813369428579614193015028249821853347208001645148169449968882591709833452960545988520048722323580338213590245476892223967673180144525106292453573842357322398199104132677638909964034937501684668442732786408572501007756270725934445316827054687741612177409932320532825182104820899546084015733164816993674100635828218335112393003462442685677115798304835391938681 c1 = 786426913645332991929803636719878643130489430090701482974255190570111407517277263761161970232982615374753982050075781017755721714929721429185828101898786972242994012456972241276851428750970754773002966788642795040933520662931514953660571657013642671173456750800960592586345219252277575624120271330470724245201080094330964145796872211627254805407394764183615099525852600855622089361965086460279057625205099471122036599934609091062009161119885692567925924978687256063116915630947838112126347748759078024890458539541208153526564434483654508834147071166870006117573542198238493913144419569943131642262575848786399020602 c2 = 14269311999815379511888097227418748728398011595172649708273598243317106830139061994801598925448165045032084910971094414749744701731066555194159863759072739031915833091715422787808666326235589236328864675164322734119047182014621724868200908222400504845559290620275973427127376594365043386362821355037781568524903149101953873768462097165128186788759111090267131443645126715520994688945363059795513931799317608292977574376954729552861360597103229877031117089231816770880909815561950691603994439997197261395452797893557057320175747162837857668062550646101714062365530246698404923128445182100334335447738834779014705114350 c3 = 3204718091370324153305164801961074660508922478706979436653573192321723216725523523538914956544950802616295043619768261075799875855502834749045520466140056621489305006966280527055668378303630674311102581232313032585389907028715671091914904062961720585667564982641321454541632782484415075257140508738041786400512095949826279576159569786734978545737717138115729502475357594151593143140355121154223614868465202149338507796306863351134218879326031985027900678671697876083351974546516576983143592764763925335805465720148057651958521255276602933604064541840892578409973858867533575728482926007556060584654853884046046420855 e = 17n = [n1, n2, n3]c = [c1, c2, c3]N = 1for i in n: N = N * im_e = 0 # m的e次方for i in range(len(n)): m_e = m_e + c[i] * N // n[i] * gmpy2.invert(N // n[i], n[i])m_e = m_e % Nm, f = gmpy2.iroot(m_e, e)flag = libnum.n2s(int(m))print("??:",flag)# ??:SICTF{fdc0afb5-1c81-46b9-a28a-241f5f64419d}
三、MingTianPao
题目信息:
这个题目名充分表现了作者由于学CTF导致吃不上饭,明天就打算跑路的心里想法。
附件信息:
import binasciifrom Crypto.Util.strxor import strxorfrom secret import flag, message# message is a Classic English Storyfor i in range(10): tmp = (message[i*30:(i+1)*30].encode()) print(binascii.hexlify(strxor(tmp,flag)).decode())# 1f2037202a1e6d06353b61263d050a0538493b3018544e14171d2b1c4218# 3769373b66142f31297f291126410e042b01162d59103a0c005221075013# 37242c202e1e3f743c36371130410c1e2b491a31574406014505291a550e# 7f6922742e1a213270372e01264105193004532b1f554e120c1e2a145618# 7d69143c23156d18392b35183141310e3b49213613590003453a291a555d# 36273731341e297424372454230e0c0f2c49127f005f020245112718545d# 26396320295b2531227161273c04430f360d533118444e0f0b1d31554615# 323d6335660c24373b3a2554350f0a063e05533712101905165e66145f19# 733e222766152220703e27063508074b300f53371e5d40444735291a555d# 37283a7432146d2d3f2a6d541808171f330c530d12544e360c162f1b565d
典型的邮件传输协议题目,我们可以发现有提示:
# message is a Classic English Story
我们知道flag的前六个字符:“SICTF{“ ,因此我们可以使用第一串信息异或一下:

根据附件里的英文提示可以猜测这是一个Little开头的英语故事(我们可以百度搜索这些故事来进行测试),根据异或的可逆性,把密文和明文互换位置

经过尝试发现Little Red Riding Hood可行

看到快出结果了,只不过结尾缺了一点而已。。。猜测应该是wonderful的变形,那么再把flag换到上面来进行测试:(因为wonderful可以进行大小写、以及形近数字变化,所以我们需要一个字符一个字符进行测试,试几次就出来了):

SICTF{MTP_AtTack_is_w0nderFu1}
这题还是挺有意思的。。。。
四、Easy_CopperSmith
题目信息:
你知道CopperSmith吗?
附件信息:
查看代码
from Crypto.Util.number import *from flag import flagp = getPrime(512)q = getPrime(512)n = p * qe = 65537leak = p >> 230m = bytes_to_long(flag)c = pow(m,e,n)print(n)print(leak)print(c)'''114007680041157617250208809154392208683967639953423906669116998085115503737001019559692895227927818755160444076128820965038044269092587109196557720941716578025622244634385547194563001079609897387390680250570961313174656874665690193604984942452581886657386063927035039087208310041149977622001887997061312418381683352568008376720156338355325736540388927586118006914927237778867184572092141013717787627846271126693177889082381507430884663777705438987267317070845965070209704910716182088690758208915234427170455157948022843849997441546596567189456637997191173043345521331111329110083529853409188141263211030032553825858341099759209550785745319223409181813931086979471131074015406202979668575990074985441810'''
经典的p高位泄漏,首先还原p以及解出q。
n = 114007680041157617250208809154392208683967639953423906669116998085115503737001019559692895227927818755160444076128820965038044269092587109196557720941716578025622244634385547194563001079609897387390680250570961313174656874665690193604984942452581886657386063927035039087208310041149977622001887997061312418381p4 = 6833525680083767201563383553257365403889275861180069149272377788671845720921410137177c = 87627846271126693177889082381507430884663777705438987267317070845965070209704910716182088690758208915234427170455157948022843849997441546596567189456637997191173043345521331111329110083529853409188141263211030032553825858341099759209550785745319223409181813931086979471131074015406202979668575990074985441810e = 65537pbits = 512kbits=pbits - p4.nbits()p4 = p4 << kbitsPR.<x> = PolynomialRing(Zmod(n))f = x + p4roots = f.small_roots(X=2^kbits,beta=0.4,epsilon = 0.01)if roots: p= p4 + int(roots[0]) q = n//pprint(p)print(q)
117908152245544108001211041879054684703901942899696165471140512824022541645137602625260482290969235794107131900068836040690133039045093831222101018119007739669194018386129503300336046235270996644150320805133719133058178879526640870171636400065553651340295023059145408424451034627123286813490640124073749725897
得到p和q后直接梭即可exp:
#解密脚本:import gmpy2from Crypto.Util.number import long_to_bytesp = 11790815224554410800121104187905468470390194289969616547114051282402254164513760262526048229096923579410713190006883604069013303904509383122210101811900773q = 9669194018386129503300336046235270996644150320805133719133058178879526640870171636400065553651340295023059145408424451034627123286813490640124073749725897c = 87627846271126693177889082381507430884663777705438987267317070845965070209704910716182088690758208915234427170455157948022843849997441546596567189456637997191173043345521331111329110083529853409188141263211030032553825858341099759209550785745319223409181813931086979471131074015406202979668575990074985441810phi = (p-1) * (q-1)e = 65537n = p * qd = gmpy2.invert(e, phi)m = pow(c, d, n)print('??:',long_to_bytes(m))
??: b'SICTF{3f9366ed-b8e4-412f-bbd0-62616a24115c}'
五、签到题来咯!
题目信息:
签到题来咯!
附件信息:
from secret import flagfrom Crypto.Util.number import *m = bytes_to_long(flag)p = getPrime(1024)q = getPrime(1024)e = getPrime(10)n = p*qc1 = pow(114*m+2333,e,n)c2 = pow(514*m+4555,e,n)print(f'n = {n}')print(f'c1 = {c1}')print(f'c2 = {c2}')'''n = 18993579800590288733556762316465854395650778003397512624355925069287661487515652428099677335464809283955351330659278915073219733930542167360381688856732762552737791137784222098296804826261681852699742456526979985201331982720936091963830799430264680941164508709453794113576607749669278887105809727027129736803614327631979056934906547015919204770702496676692691248702461766117271815398943842909579917102217310779431999448597899109808086655029624478062317317442297276087073653945439820988375066353157221370129064423613949039895822016206336117081475698987326594199181180346821431242733826487765566154350269651592993856883c1 = 3089900890429368903963127778258893993015616003863275300568951378177309984878857933740319974151823410060583527905656182419531008417050246901514691111335764182779077027419410717272164998075313101695833565450587029584857433998627248705518025411896438130004108810308599666206694770859843696952378804678690327442746359836105117371144846629293505396610982407985241783168161504309420302314102538231774470927864959064261347913286659384383565379900391857812482728653358741387072374314243068833590379370244368317200796927931678203916569721211768082289529948017340699194622234734381555103898784827642197721866114583358940604520c2 = 6062491672599671503583327431533992487890060173533816222838721749216161789662841049274959778509684968479022417053571624473283543736981267659104310293237792925201009775193492423025040929132360886500863823523629213703533794348606076463773478200331006341206053010168741302440409050344170767489936681627020501853981450212305108039373119567034948781143698613084550376070802084805644270376620484786155554275798939105737707005991882264123315436368611647275530607811665999620394422672764116158492214128572456571553281799359243174598812137554860109807481900330449364878168308833006964726761878461761560543284533578701661413931'''
典型的明文相关攻击,只不过稍微变化了一下。
解题思路:
首先需要列出两个多项式,因为明文m是两个模多项式的根,因此两个模多项式有公因子;构造出模n环下的两个多项式,并求公因式即可。至于e是多少,仅需要在指定范围内爆破一下就可以。
exp:
from gmpy2 import *from Crypto.Util.number import *n = 18993579800590288733556762316465854395650778003397512624355925069287661487515652428099677335464809283955351330659278915073219733930542167360381688856732762552737791137784222098296804826261681852699742456526979985201331982720936091963830799430264680941164508709453794113576607749669278887105809727027129736803614327631979056934906547015919204770702496676692691248702461766117271815398943842909579917102217310779431999448597899109808086655029624478062317317442297276087073653945439820988375066353157221370129064423613949039895822016206336117081475698987326594199181180346821431242733826487765566154350269651592993856883c1 = 3089900890429368903963127778258893993015616003863275300568951378177309984878857933740319974151823410060583527905656182419531008417050246901514691111335764182779077027419410717272164998075313101695833565450587029584857433998627248705518025411896438130004108810308599666206694770859843696952378804678690327442746359836105117371144846629293505396610982407985241783168161504309420302314102538231774470927864959064261347913286659384383565379900391857812482728653358741387072374314243068833590379370244368317200796927931678203916569721211768082289529948017340699194622234734381555103898784827642197721866114583358940604520c2 = 6062491672599671503583327431533992487890060173533816222838721749216161789662841049274959778509684968479022417053571624473283543736981267659104310293237792925201009775193492423025040929132360886500863823523629213703533794348606076463773478200331006341206053010168741302440409050344170767489936681627020501853981450212305108039373119567034948781143698613084550376070802084805644270376620484786155554275798939105737707005991882264123315436368611647275530607811665999620394422672764116158492214128572456571553281799359243174598812137554860109807481900330449364878168308833006964726761878461761560543284533578701661413931a1 = 114b1 = 2333a2 = 514b2 = 4555elist = [521,523,541,547,557,563,569,571,577,587,593,599,601,607,613,617,619,631,641,643,647,653,659,661,673,677,683,691,701,709,719,727,733,739,743,751,757,761,769,773,787,797,809,811,821,823,827,829,839,853,857,859,863,877,881,883,887,907,911,919,929,937,941,947,953,967,971,977,983,991,997,1009,1013,1019,1021]def attack(c1, c2, e, n): PR.<x>=PolynomialRing(Zmod(n)) g1 = (a1*x + b1)^e - c1 g2 = (a2*x + b2)^e - c2 def gcd(g1, g2): while g2: g1, g2 = g2, g1 % g2 return g1.monic() return -gcd(g1, g2)[0]for e in elist: m1 = attack(c1, c2, e, n) if(b"SICTF" in long_to_bytes(int(m1))): flag = long_to_bytes(int(m1)) print(flag)
SICTF{hhh!!franklin_reiter_is_easy}
六、small_e
题目信息:
这个低加密指数攻击为什么打不出来哇?是不是题有问题捏?差评!
附件信息:
import libnumfrom Crypto.Util.number import *import uuidflag="SICTF{"+str(uuid.uuid4())+"}"m=libnum.s2n(flag)p=getPrime(1024)q=getPrime(1024)n=p*qe=3c=pow(m,e,n)m1=((m>>60)<<60)print("n=",n)print("e=",e)print("c=",c)print("((m>>60)<<60)=",m1)print(flag)'''n= 23407088262641313744603678186127228163189328033499381357614318160776774708961658114505773173784501557046914457908828086210961235530240151825359345210845219656000760996670856300710703016947799649686427460688236465568188205550456293373157997725204643414082796492333552579250010906010553831060540937802882205118399938918764313169385349293602085310111289583058965780887097301702677087443291977479125263301000328313103296364864396361278863921717374909215078711198899810620522933994481419395021233240234478331179727351050575360886334237633420906629984625441302945112631166021776379103081857393866576659121443879590011160797e= 3c= 1584727211980974717747362694412040878682966138197627512650829607105625096823456063149392973232737929737200028676411430124019573130595696272668927725536797627059576270068695792221537212669276826952363636924278717182163166234322320044764324434683614360641636360301452618063418349310497430566465329766916213742181((m>>60)<<60)= 11658736990073967239197168945911788935424691658202162501032766529463315401599017877851823976178979438592'''
小明文攻击,直接上脚本:
import gmpy2from Crypto.Util.number import long_to_bytesn =23407088262641313744603678186127228163189328033499381357614318160776774708961658114505773173784501557046914457908828086210961235530240151825359345210845219656000760996670856300710703016947799649686427460688236465568188205550456293373157997725204643414082796492333552579250010906010553831060540937802882205118399938918764313169385349293602085310111289583058965780887097301702677087443291977479125263301000328313103296364864396361278863921717374909215078711198899810620522933994481419395021233240234478331179727351050575360886334237633420906629984625441302945112631166021776379103081857393866576659121443879590011160797e =3c =1584727211980974717747362694412040878682966138197627512650829607105625096823456063149392973232737929737200028676411430124019573130595696272668927725536797627059576270068695792221537212669276826952363636924278717182163166234322320044764324434683614360641636360301452618063418349310497430566465329766916213742181m = gmpy2.iroot(c,e)[0]print('???: ',long_to_bytes(m))#???:SICTF{2ca8e589-4a31-4909-80f0-9ecfc8f8cb37}
七、easy_math
题目信息:
其实数学很简单辣!
附件信息:
from secret import flagfrom Crypto.Util.number import *m = bytes_to_long(flag)p = getPrime(512)q = getPrime(512)n = p * qe = 65537hint1 = getPrime(13)*p+getPrime(256)*qhint2 = getPrime(13)*p+getPrime(256)*qc = pow(m,e,n)print(f'n = {n}')print(f'hint1 = {hint1}')print(f'hint2 = {hint2}')print(f'c = {c}')'''n = 68123067052840097285002963401518347625939222208495512245264898037784706226045178539672509359795737570458454279990340789711761542570505016930986418403583534761200927746744298082254959321108829717070206277856970403191060311901559017372393931121345743640657503994132925993800497309703877076541759570410784984067hint1 = 564294243979930441832363430202216879765636227726919016842676871868826273613344463155168512928428069316237289920953421495330355385445649203238665802121198919543532254290185502622234014832349396422316629991217252686524462096711723580hint2 = 484307144682854466149980416084532076579378210225500554261260145338511061452958092407101769145891750844383042274498826787696953308289632616886162073232218214504005935332891893378072083589751354946391146889055039887781077066257013110c = 57751903193610662622957432730720223801836323458721550133101805763463060486486266309568004721657732742899781400754207249733137375171400440423755473421971160000575072519031824740691618617905549725344323721903857290320737224300672847773455169809689188843070599176261204013341324705808617411345132933937680951713'''
给出了hint1、hint2的生成过程:
p前的两个系数很小,因此可以先打印出所有13比特的素数存在一张表内,作为系数的所有可能取值,然后与n求gcd即可得到q,之后进行RSA解密即可。
exp:
from Crypto.Util.number import *n = 68123067052840097285002963401518347625939222208495512245264898037784706226045178539672509359795737570458454279990340789711761542570505016930986418403583534761200927746744298082254959321108829717070206277856970403191060311901559017372393931121345743640657503994132925993800497309703877076541759570410784984067hint1 = 564294243979930441832363430202216879765636227726919016842676871868826273613344463155168512928428069316237289920953421495330355385445649203238665802121198919543532254290185502622234014832349396422316629991217252686524462096711723580hint2 = 484307144682854466149980416084532076579378210225500554261260145338511061452958092407101769145891750844383042274498826787696953308289632616886162073232218214504005935332891893378072083589751354946391146889055039887781077066257013110c = 57751903193610662622957432730720223801836323458721550133101805763463060486486266309568004721657732742899781400754207249733137375171400440423755473421971160000575072519031824740691618617905549725344323721903857290320737224300672847773455169809689188843070599176261204013341324705808617411345132933937680951713e = 65537primelist = [i for i in range(2**12,2**13) if isPrime(i)]for i in primelist: for j in primelist: if(GCD(hint1*i - hint2*j,n) != 1): q = GCD(hint1*i - hint2*j,n)p = n//qd = inverse(e,(p-1)*(q-1))m = pow(c,d,n)print(long_to_bytes(m))
SICTF{452aebb6-9c16-441a-ac42-fc608bf6063f}
??Misc
一、[签到]Welcome
题目信息:
关注微信公众号并发送"SICTF2023"就可以获得flag辣!
解题方法:
关注公众号按要求来即可
SICTF{Welcome_to_SICTF2023_#Round2}
二、Pixel_art
题目信息:
这张颜色很奇怪的图片到底是干什么的呢?
解题方法:
下载附件,是一个zip压缩包,解密提示需要密码,010打开并未找到密码,因此想到是伪加密。修改对应位置进制即可:


将此处01改为00即可解压得到下面图片。

查看图片信息:
# 从Pillow库导入Image类from PIL import Image# 读取本地文件名为1.png的图片img = Image.open('2.png')# size 记录了图片的宽、高,单位为像素(px)width, height = img.sizeprint(width, height) # 256 256# mode 属性记录了图片使用的图片模式mode = img.modeprint(img.mode) # RGBA# getpixel()方法接受一个元组,元组中为要获取像素信息的像素点坐标# PIL使用笛卡尔像素坐标系统,坐标(0,0)位于左上角# X轴是从左到右增长的,Y轴是从上到下增长, 可以自己上手试试.x, y = 100, 100pix = img.getpixel((x, y))print(pix) # (1, 67, 145, 235)# 也可以使用load方法,该方法返回所有像素点的信息pix = img.load()print(pix[x, y]) # (1, 67, 145, 235)
1000 1000RGBA(42, 49, 53, 255)(42, 49, 53, 255)
想到LSB隐写:

发现藏了东西,保存为png文件后查看:

这图好小嘿嘿嘿!!,查看其详细信息:

20*20的,想到flag被加密进了像素点里。脚本提取像素点:
from PIL import Imageimage = Image.open('3.png') # 替换为你的图片文件路径width, height = image.sizepixel_data = []for y in range(height): for x in range(width): pixel = image.getpixel((x, y)) pixel_data.append(pixel)print(pixel_data)
[(46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (33, 63, 33), (33, 46, 63), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (63, 46, 63), (33, 46, 63), (46, 46, 46), (46, 33, 46), (63, 46, 46), (46, 46, 46), (46, 46, 33), (63, 33, 33), (46, 63, 33), (33, 33, 33), (33, 33, 63), (46, 63, 33), (46, 63, 33), (33, 33, 46), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 46, 63), (46, 46, 46), (46, 46, 46), (46, 46, 46), (33, 63, 33), (33, 46, 63), (46, 46, 46), (46, 46, 46), (46, 46, 63), (46, 63, 33), (46, 63, 46), (46, 33, 46), (63, 46, 46), (46, 46, 46), (46, 46, 33), (63, 33, 33), (46, 63, 33), (33, 33, 33), (33, 33, 63), (46, 63, 33), (46, 63, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 46, 63), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (33, 63, 33), (33, 46, 63), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 63), (46, 63, 33), (46, 63, 46), (46, 46, 46), (46, 46, 46), (46, 33, 46), (63, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (33, 63, 33), (33, 46, 63), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 63, 46), (63, 33, 46), (63, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (46, 46, 46), (33, 46, 46), (46, 46, 46), (46, 46, 33), (46, 33, 33), (33, 33, 33), (33, 33, 46), (63, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 33), (63, 33, 33), (46, 63, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 63), (46, 63, 33), (46, 63, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 33), (46, 46, 46), (46, 46, 33), (46, 63, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (33, 63, 33), (33, 46, 63), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (63, 46, 63), (33, 46, 63), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 46, 46), (46, 46, 46), (33, 46, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 46, 63), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (33, 63, 33), (33, 46, 63), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 63), (46, 63, 33), (46, 63, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 33, 46), (33, 33, 33), (33, 33, 46), (63, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 33, 63), (33, 33, 46), (63, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (63, 46, 63), (33, 46, 63), (33, 33, 33), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 33), (46, 63, 46), (46, 46, 46), (46, 46, 46), (33, 63, 33), (33, 46, 63), (33, 33, 33), (33, 33, 33), (63, 46, 63), (33, 46, 63), (33, 33, 33), (33, 33, 33), (33, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 33, 46), (63, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 33), (63, 33, 33), (46, 63, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 63), (46, 63, 33), (46, 63, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (33, 46, 46), (46, 46, 46), (33, 46, 33), (46, 63, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 33), (63, 33, 33), (46, 63, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 63, 46), (63, 33, 46), (63, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 46, 63), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (33, 63, 33), (33, 46, 63), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 63), (46, 63, 33), (46, 63, 46), (46, 46, 46), (46, 46, 33), (46, 63, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (33, 63, 33), (33, 46, 63), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (63, 46, 63), (33, 46, 63), (33, 33, 33), (33, 33, 33), (33, 33, 33), (46, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (33, 46, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 33), (46, 33, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (33, 46, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (33, 46, 63), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (33, 63, 33), (33, 46, 63), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 63), (46, 63, 33), (46, 63, 33), (46, 33, 33), (33, 33, 33), (46, 33, 33), (33, 33, 33), (46, 46, 46), (46, 46, 46), (46, 33, 46), (33, 33, 33), (46, 63, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (33, 63, 33), (33, 46, 63), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (63, 46, 63), (33, 46, 63), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 33, 33), (33, 46, 33), (46, 63, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 33, 63), (33, 33, 46), (63, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 63), (46, 63, 33), (46, 63, 46), (46, 46, 46), (46, 46, 46), (46, 46, 46), (46, 46, 33), (46, 63, 46), (0, 0, 0), (0, 0, 0), (0, 0, 0), (0, 0, 0), (0, 0, 0), (0, 0, 0), (0, 0, 0), (0, 0, 0)]
一共得到的三个数字显然有特殊含义,当作ASCII码打印出对应字符发现:
46-. 33-!63-?
哈哈,一看就是Ook加密,写个完整脚本生成Ook密文:
from PIL import Imageimage = Image.open('3.png') # 替换为你的图片文件路径width, height = image.sizepixel_data = []for y in range(height): for x in range(width): pixel = image.getpixel((x, y)) pixel_data.append(pixel)count = 0for i in range(len(pixel_data)): if(pixel_data[i] == (0,0,0)): break for j in pixel_data[i]: print("Ook"+chr(j),end = "")
得到:
Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook?Ook!Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook?Ook.Ook?Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook?Ook!Ook!Ook.Ook?Ook!Ook!Ook!Ook!Ook!Ook!Ook?Ook.Ook?Ook!Ook.Ook?Ook!Ook!Ook!Ook.Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook?Ook!Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook?Ook.Ook?Ook!Ook.Ook?Ook.Ook.Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook?Ook!Ook!Ook.Ook?Ook!Ook!Ook!Ook!Ook!Ook!Ook?Ook.Ook?Ook!Ook.Ook?Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook?Ook!Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook?Ook.Ook?Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook?Ook!Ook!Ook.Ook?Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook?Ook.Ook?Ook!Ook.Ook?Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook.Ook.Ook.Ook!Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook.Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook?Ook!Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook?Ook.Ook?Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook.Ook.Ook.Ook.Ook.Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook?Ook!Ook!Ook.Ook?Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook?Ook.Ook?Ook!Ook.Ook?Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook.Ook.Ook.Ook.Ook.Ook!Ook.Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook?Ook!Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook?Ook.Ook?Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook.Ook!Ook!Ook!Ook!Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook?Ook!Ook!Ook.Ook?Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook?Ook.Ook?Ook!Ook.Ook?Ook!Ook!Ook!Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook?Ook!Ook!Ook.Ook?Ook!Ook!Ook!Ook!Ook!Ook!Ook?Ook.Ook?Ook!Ook.Ook?Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook?Ook!Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook?Ook.Ook?Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook.Ook.Ook.Ook.Ook.Ook!Ook.Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook?Ook!Ook!Ook.Ook?Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook?Ook.Ook?Ook!Ook.Ook?Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook?Ook!Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook?Ook.Ook?Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook?Ook!Ook!Ook.Ook?Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook?Ook.Ook?Ook!Ook.Ook?Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook.Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook.Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook.Ook!Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook.Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook?Ook!Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook?Ook.Ook?Ook!Ook.Ook?Ook!Ook.Ook!Ook!Ook!Ook!Ook!Ook.Ook!Ook!Ook!Ook!Ook!Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook.Ook!Ook!Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook?Ook!Ook!Ook.Ook?Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook?Ook.Ook?Ook!Ook.Ook?Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook!Ook.Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook?Ook!Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook?Ook.Ook?Ook!Ook.Ook?Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook.Ook!Ook.Ook?Ook.
在线工具解密:

SICTF{0141ac35-ec19-4cee-a906-22805fdbed77}
三、一起上号不
题目信息:
你为什么还不上号啊?宝!
提示:你知道CobaltStrike吗?
解题方法:
题目给了一个流量包,导出http流对象,可以发现一个key.zip:

导出该压缩包并解压,得到一个key文件,我们需要提取出key中的信息,根据hint,我们直接搜索CobaltStrike,发现了一道类似流量分析题,照着一步一步做就行了:
https://blog.csdn.net/qq_43264813/article/details/120560209
最终得到flag:
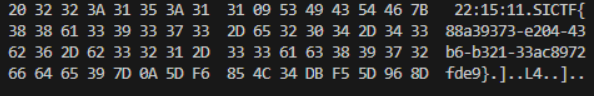
SICTF{88a39373-e204-43b6-b321-33ac8972fde9}
四、baby_zip
题目信息:
攻破这个压缩包!
题目给了一个压缩包,首先检查出是真加密,然后尝试ziprello爆破无果,binwalk也没有分离出其他文件,那么猜测只能是深入明文攻击了。
相关方法可以参考:
https://hasegawaazusa.github.io/zip-crack-note.html#zip-%E7%A0%B4%E8%A7%A3
明文攻击需要至少12个已知字节。由于已知压缩包内为png文件,知道文件头:
89 50 4E 47 0D 0A 1A 0A 00 00 00 0D 49 48 44 52
因此,我们至少知道了16个准确的字节,超过了12个字节,已经满足深入明文攻击的条件了,(多的已知字节可以加快速度),接下来就使用工具即可。
首先生成明文文件:

随后进行密钥爆破:
bkcrack -C flag.zip -c flag.png -p key.txt -o 0

得到三段密钥后我们进行提取
bkcrack -C flag.zip -c flag.png -k 6424c164 7c334afd f99666e5 -d flag1.png
得到图片:

010打开拉到末尾即得flag:
SICTF{3a4998b8-345e-4943-a689-d01e8b08defb}
五、还不上号
题目信息:
一起上号不?来!我教你怎么写payload!Hint1:四位爆破,多注意一下细节,除了CS还有一部分Hint2:压缩包密码为we1l
其实这道题就是Easy_shark和一起上号不的结合,这两个都做出来的话,这题其实难度不大了。
题目给了两个流量包,由名字可以知道一个包对应一半flag。其中,包1形式对应Ez_shark,包2形式对应一起上号不。
从包1入手,可以发现对比起Ez_shark,唯一的区别就是他没有给出AES的key值,因此必须要想办法找出key。而包2正好有个key.zip,进行导出:

得到的key.zip不能直接解压,并且是真加密,同时也没法进行明文攻击,那么就ziprello爆破吧,最后得到密码是we1l(并且后来Hint给了)。
打开key文件发现有零宽字符,利用在线网站http://330k.github.io/misc_tools/unicode_steganography.html进行零宽字符解密:

这里要注意在网页下方勾选该文本中所有存在的零宽字符,不然解密会失败:

因此就得到了AES的key,可以按照Ez_Shark的方式对包1的流量依次进行解密,能得到两个有用信息:
flag.txt:
SICTF{79e1755e-08a8-4d
key:

如果做出来一起上号不那道题,那么对这串数据应该很熟悉,这就是.cobaltstrike.beacon_keys形式的密钥文件,将这段内容保存成文件key1.txt,后续的步骤就和前面那道题就一模一样了。
下面详细记录一下步骤:
1、解析key1.txt文件得到private_key
import base64import javaobj.v2 as javaobjwith open("key1.txt", "rb") as fd: pobj = javaobj.load(fd)privateKey = pobj.array.value.privateKey.encoded.datapublicKey = pobj.array.value.publicKey.encoded.dataprivateKey = ( b"-----BEGIN PRIVATE KEY-----\n" + base64.encodebytes(bytes(map(lambda x: x & 0xFF, privateKey))) + b"-----END PRIVATE KEY-----")publicKey = ( b"-----BEGIN PUBLIC KEY-----\n" + base64.encodebytes(bytes(map(lambda x: x & 0xFF, publicKey))) + b"-----END PUBLIC KEY-----")print(privateKey.decode())print(publicKey.decode())# print(# list(# map(# lambda x: list(map(lambda y: (y[0].name, y[1]), x.items())),# a.field_data.values(),# )# )# )
2、根据private_key以及流量包中cookie解析出AES key和HMAC key:(其他信息有需要,解除掉注释即可,这里只需要AES与HMAC的key)
import hashlibfrom Crypto.PublicKey import RSAfrom Crypto.Cipher import PKCS1_v1_5import base64import hexdump PRIVATE_KEY = """-----BEGIN PRIVATE KEY-----MIICdgIBADANBgkqhkiG9w0BAQEFAASCAmAwggJcAgEAAoGBAL0M6FR0Cb9dW52Nd5NTA1JUNAs1thS8iXx6QB+UkN/vRJdfsKS8dnOfNuPuPDCtx26B2j8I1FuTJ1VrrfDkzN585sskmXYronFM98Dx50vHaadOcDcDdBBqi8gC5/D3iKflX6T9pSL/5PVLfN1EIaFsyAS9jpWX2wGNi3C/QPSrAgMBAAECgYAdNhXeGtH4wkWqOhY8aurL+VvTUZjRanJ6C+/FkXCzUWbRVwVV5xMMeZEDNigRw4BZ2HGvJL+faMT+o3VMkCYBhGbi2/3RPRgigMG7Aa3LWWtYWsdbw8Mw6aqqbTjDUHrQ1kulMf1JvXJL5LBd+pBAQ8kHaYJRMcmnLsT4NeXOFQJBAMNa2r+phrThTlagMB6bj6vl0IVbDy+TJT2VybCSJ76rPgVUQwtPyX3z7UAjt27mE8KK+k7Jidi0drCEPv5Wo60CQQD3vQbO64fko1dlatkNn095GO9KoCuanrsLs+vY Ohc0ltk4EhHHmP5hEE6dSMZNASKaN0wSYJ14xjnA+dJWOES3AkEApzyYF4vhLefTUIVBrHIvxFCw +fjCP1AQiXA5gVcdfzTJm3ZPDtf2/kRbzpTE68M7F0gykFAoGcQj92i/JKy24QJAdyVbA+M07Ro9 qxHzJ+EJmMUMOMjFj8xtStiSQeDWTj2KZLQUBvmmxcnQ9UYN0PUNzjtwA5qhwXccSZoctcjECwJA Zc0TZgGq/OwgnIyj/1+Q9D0A2eg3aw1k+6Vzkf/DdkuF6+XTkYTlBGiETIK/vm1rCH4NcOCL7eK5 qpA1grg+gg==-----END PRIVATE KEY-----""" encode_data = "j+ojKDVPlCr7lT9yzNinkj1DgdkcRaLMT2kL4U+9TvdFBZqGKk7/4WF/W7JhEieC3DoRfngRppMAVHa3yfhp4HZm/ZeNY4bc8rlYL11Q0dXDzpR5JjhqN+hGe9RBqPznoukShgQLhxT/DO7djxE5ROzi6NC52yZAaGPCSeLDyjg="base64_key = """""" private_key = RSA.import_key(PRIVATE_KEY.format(base64_key).encode())cipher = PKCS1_v1_5.new(private_key)ciphertext = cipher.decrypt(base64.b64decode(encode_data), 0)def isFlag(var, flag): return (var & flag) == flagdef toIP(var): var2 = (var & -16777216) >> 24 var4 = (var & 16711680) >> 16 var6 = (var & 65280) >> 8 var8 = var & 255 return str(var2) + "." + str(var4) + "." + str(var6) + "." + str(var8)def getName(var0): if var0 == 37: return "IBM037" elif var0 == 437: return "IBM437" elif var0 == 500: return "IBM500" elif var0 == 708: return "ISO-8859-6" elif var0 == 709: return "" elif var0 == 710: return "" elif var0 == 720: return "IBM437" elif var0 == 737: return "x-IBM737" elif var0 == 775: return "IBM775" elif var0 == 850: return "IBM850" elif var0 == 852: return "IBM852" elif var0 == 855: return "IBM855" elif var0 == 857: return "IBM857" elif var0 == 858: return "IBM00858" elif var0 == 860: return "IBM860" elif var0 == 861: return "IBM861" elif var0 == 862: return "IBM862" elif var0 == 863: return "IBM863" elif var0 == 864: return "IBM864" elif var0 == 865: return "IBM865" elif var0 == 866: return "IBM866" elif var0 == 869: return "IBM869" elif var0 == 870: return "IBM870" elif var0 == 874: return "x-windows-874" elif var0 == 875: return "IBM875" elif var0 == 932: return "Shift_JIS" elif var0 == 936: return "x-mswin-936" elif var0 == 949: return "x-windows-949" elif var0 == 950: return "Big5" elif var0 == 1026: return "IBM1026" elif var0 == 1047: return "IBM1047" elif var0 == 1140: return "IBM01140" elif var0 == 1141: return "IBM01141" elif var0 == 1142: return "IBM01142" elif var0 == 1143: return "IBM01143" elif var0 == 1144: return "IBM01144" elif var0 == 1145: return "IBM01145" elif var0 == 1146: return "IBM01146" elif var0 == 1147: return "IBM01147" elif var0 == 1148: return "IBM01148" elif var0 == 1149: return "IBM01149" elif var0 == 1200: return "UTF-16LE" elif var0 == 1201: return "UTF-16BE" elif var0 == 1250: return "windows-1250" elif var0 == 1251: return "windows-1251" elif var0 == 1252: return "windows-1252" elif var0 == 1253: return "windows-1253" elif var0 == 1254: return "windows-1254" elif var0 == 1255: return "windows-1255" elif var0 == 1256: return "windows-1256" elif var0 == 1257: return "windows-1257" elif var0 == 1258: return "windows-1258" elif var0 == 1361: return "x-Johab" elif var0 == 10000: return "x-MacRoman" elif var0 == 10001: return "" elif var0 == 10002: return "" elif var0 == 10003: return "" elif var0 == 10004: return "x-MacArabic" elif var0 == 10005: return "x-MacHebrew" elif var0 == 10006: return "x-MacGreek" elif var0 == 10007: return "x-MacCyrillic" elif var0 == 10008: return "" elif var0 == 10010: return "x-MacRomania" elif var0 == 10017: return "x-MacUkraine" elif var0 == 10021: return "x-MacThai" elif var0 == 10029: return "x-MacCentralEurope" elif var0 == 10079: return "x-MacIceland" elif var0 == 10081: return "x-MacTurkish" elif var0 == 10082: return "x-MacCroatian" elif var0 == 12000: return "UTF-32LE" elif var0 == 12001: return "UTF-32BE" elif var0 == 20000: return "x-ISO-2022-CN-CNS" elif var0 == 20001: return "" elif var0 == 20002: return "" elif var0 == 20003: return "" elif var0 == 20004: return "" elif var0 == 20005: return "" elif var0 == 20105: return "" elif var0 == 20106: return "" elif var0 == 20107: return "" elif var0 == 20108: return "" elif var0 == 20127: return "US-ASCII" elif var0 == 20261: return "" elif var0 == 20269: return "" elif var0 == 20273: return "IBM273" elif var0 == 20277: return "IBM277" elif var0 == 20278: return "IBM278" elif var0 == 20280: return "IBM280" elif var0 == 20284: return "IBM284" elif var0 == 20285: return "IBM285" elif var0 == 20290: return "IBM290" elif var0 == 20297: return "IBM297" elif var0 == 20420: return "IBM420" elif var0 == 20423: return "" elif var0 == 20424: return "IBM424" elif var0 == 20833: return "" elif var0 == 20838: return "IBM-Thai" elif var0 == 20866: return "KOI8-R" elif var0 == 20871: return "IBM871" elif var0 == 20880: return "" elif var0 == 20905: return "" elif var0 == 20924: return "" elif var0 == 20932: return "EUC-JP" elif var0 == 20936: return "GB2312" elif var0 == 20949: return "" elif var0 == 21025: return "x-IBM1025" elif var0 == 21027: return "" elif var0 == 21866: return "KOI8-U" elif var0 == 28591: return "ISO-8859-1" elif var0 == 28592: return "ISO-8859-2" elif var0 == 28593: return "ISO-8859-3" elif var0 == 28594: return "ISO-8859-4" elif var0 == 28595: return "ISO-8859-5" elif var0 == 28596: return "ISO-8859-6" elif var0 == 28597: return "ISO-8859-7" elif var0 == 28598: return "ISO-8859-8" elif var0 == 28599: return "ISO-8859-9" elif var0 == 28603: return "ISO-8859-13" elif var0 == 28605: return "ISO-8859-15" elif var0 == 29001: return "" elif var0 == 38598: return "ISO-8859-8" elif var0 == 50220: return "ISO-2022-JP" elif var0 == 50221: return "ISO-2022-JP-2" elif var0 == 50222: return "ISO-2022-JP" elif var0 == 50225: return "ISO-2022-KR" elif var0 == 50227: return "ISO-2022-CN" elif var0 == 50229: return "ISO-2022-CN" elif var0 == 50930: return "x-IBM930" elif var0 == 50931: return "" elif var0 == 50933: return "x-IBM933" elif var0 == 50935: return "x-IBM935" elif var0 == 50936: return "" elif var0 == 50937: return "x-IBM937" elif var0 == 50939: return "x-IBM939" elif var0 == 51932: return "EUC-JP" elif var0 == 51936: return "GB2312" elif var0 == 51949: return "EUC-KR" elif var0 == 51950: return "" elif var0 == 52936: return "GB2312" elif var0 == 54936: return "GB18030" elif var0 == 57002: return "x-ISCII91" elif var0 == 57003: return "x-ISCII91" elif var0 == 57004: return "x-ISCII91" elif var0 == 57005: return "x-ISCII91" elif var0 == 57006: return "x-ISCII91" elif var0 == 57007: return "x-ISCII91" elif var0 == 57008: return "x-ISCII91" elif var0 == 57009: return "x-ISCII91" elif var0 == 57010: return "x-ISCII91" elif var0 == 57011: return "x-ISCII91" elif var0 == 65000: return "" elif var0 == 65001: return "UTF-8"if ciphertext[0:4] == b'\x00\x00\xBE\xEF': # 16 raw_aes_keys = ciphertext[8:24] # 2 var9 = ciphertext[24:26] var9 = int.from_bytes(var9, byteorder='little', signed=False) var9 = getName(var9) # 2 var10 = ciphertext[26:28] var10 = int.from_bytes(var10, byteorder='little', signed=False) var10 = getName(var10) # 4 id = ciphertext[28:32] id = int.from_bytes(id, byteorder='big', signed=False) #print("Beacon id:{}".format(id)) # 4 pid = ciphertext[32:36] pid = int.from_bytes(pid, byteorder='big', signed=False) #print("pid:{}".format(pid)) # 2 port = ciphertext[36:38] port = int.from_bytes(port, byteorder='big', signed=False) #print("port:{}".format(port)) # 1 flag = ciphertext[38:39] flag = int.from_bytes(flag, byteorder='big', signed=False) # print(flag) if isFlag(flag, 1): barch = "" pid = "" is64 = "" elif isFlag(flag, 2): barch = "x64" else: barch = "x86" if isFlag(flag, 4): is64 = "1" else: is64 = "0" if isFlag(flag, 8): bypassuac = "True" else: bypassuac = "False" #print("barch:" + barch) #print("is64:" + is64) #print("bypass:" + bypassuac) # 2 var_1 = ciphertext[39:40] var_2 = ciphertext[40:41] var_1 = int.from_bytes(var_1, byteorder='big', signed=False) var_2 = int.from_bytes(var_2, byteorder='big', signed=False) windows_var = str(var_1) + "." + str(var_2) #print("windows var:" + windows_var) # 2 windows_build = ciphertext[41:43] windows_build = int.from_bytes(windows_build, byteorder='big', signed=False) #print("windows build:{}".format(windows_build)) # 4 x64_P = ciphertext[43:47] # 4 ptr_gmh = ciphertext[47:51] # 4 ptr_gpa = ciphertext[51:55] # if ("x64".equals(this.barch)) { # this.ptr_gmh = CommonUtils.join(var10, this.ptr_gmh) # this.ptr_gpa = CommonUtils.join(var10, this.ptr_gpa) # } # # this.ptr_gmh = CommonUtils.bswap(this.ptr_gmh) # this.ptr_gpa = CommonUtils.bswap(this.ptr_gpa) # 4 intz = ciphertext[55:59] intz = int.from_bytes(intz, byteorder='little', signed=False) intz = toIP(intz) if intz == "0.0.0.0": intz = "unknown" #print("host:" + intz) if var9 == None: ddata = ciphertext[59:len(ciphertext)].decode("ISO8859-1") else: # ??x-mswin-936 # ddata = ciphertext[59:len(ciphertext)].decode(var9) ddata = ciphertext[59:len(ciphertext)].decode("ISO8859-1") ddata = ddata.split("\t") if len(ddata) > 0: computer = ddata[0] if len(ddata) > 1: username = ddata[1] if len(ddata) > 2: process = ddata[2] #print("PC name:" + computer) #print("username:" + username) #print("process name:" + process) raw_aes_hash256 = hashlib.sha256(raw_aes_keys) digest = raw_aes_hash256.digest() aes_key = digest[0:16] hmac_key = digest[16:] print("AES key:{}".format(aes_key.hex())) print("HMAC key:{}".format(hmac_key.hex())) #print(hexdump.hexdump(ciphertext))
3、将流量包中数据写成base64形式:(数据指的是图中蓝色部分,每个tcp流中的流量均试一下即可)

转换为原始数据:

写成base64形式:

4、最终解密:
'''Beacon任务执行结果解密'''import hmacimport binasciiimport base64import structimport hexdumpfrom Crypto.Cipher import AESdef compare_mac(mac, mac_verif): if mac == mac_verif: return True if len(mac) != len(mac_verif): print "invalid MAC size" return False result = 0 for x, y in zip(mac, mac_verif): result |= x ^ y return result == 0def decrypt(encrypted_data, iv_bytes, signature, shared_key, hmac_key): if not compare_mac(hmac.new(hmac_key, encrypted_data, digestmod="sha256").digest()[0:16], signature): print("message authentication failed") return cypher = AES.new(shared_key, AES.MODE_CBC, iv_bytes) data = cypher.decrypt(encrypted_data) return data#key源自Beacon_metadata_RSA_Decrypt.pySHARED_KEY = binascii.unhexlify("2f793b0251bb6c09bda982cb159cd611")HMAC_KEY = binascii.unhexlify("e5695e8bf533009cd4a3c950d447b032")encrypt_data="AAAAwNR1s4ymDHA08b2cCeYKryK3UKJK0G2nKl/svxd3sD2WvktAWL1hS0gvdfXP7XmLpCd3CgYHRMvh9bWGrKW/2ANbWBQEYp1Lv+iIsuBpLdxanTNqAEOnre/71JK8hUKuJ32lY88IsDwgFFjvH0l3lwDOwgtXtOe6mhxvhuxUK8ourv/sii2KGiMOacqaRI2bOtOBcEal00/bBj85FcE+W6PmmGbF0Q9BvUvQmDT9C+J2H12SZqwwAbFGVJwntkDq7Q=="encrypt_data=base64.b64decode(encrypt_data)encrypt_data_length=encrypt_data[0:4]encrypt_data_length=int.from_bytes(encrypt_data_length, byteorder='big', signed=False)encrypt_data_l = encrypt_data[4:len(encrypt_data)]data1=encrypt_data_l[0:encrypt_data_length-16]signature=encrypt_data_l[encrypt_data_length-16:encrypt_data_length]iv_bytes = bytes("abcdefghijklmnop",'utf-8')dec=decrypt(data1,iv_bytes,signature,SHARED_KEY,HMAC_KEY)counter = dec[0:4]counter=int.from_bytes(counter, byteorder='big', signed=False)print("counter:{}".format(counter))dec_length = dec[4:8]dec_length=int.from_bytes(dec_length, byteorder='big', signed=False)print("任务返回长度:{}".format(dec_length))de_data= dec[8:len(dec)]Task_type=de_data[0:4]Task_type=int.from_bytes(Task_type, byteorder='big', signed=False)print("任务输出类型:{}".format(Task_type))print(de_data)#print(hexdump.hexdump(dec))
可以看到一串base32数据:

解密即得flag后半段:

SICTF{79e1755e-08a8-4d3d-9385-4c0541549995}
六、Easy_Shark
题目信息:
鲨鱼!嗷呜!
解题方法:
题目给了一个流量文件,追踪tcp流能发现一段php代码:

可以看出,在openssl扩展有效时,这段代码对数据的解密方式为AES_128后base64,并且给了key的值(之后了解到这是很明显的冰蝎的特征)。那么就可以使用cyberchef,对之后的每个tcp流里的base64数据进行恢复:

再把解密出来的密文内部的base64段提取出来,再进行解密,就可以在最底下发现:

可以看出,这段程序就是在执行最下方的cmd命令,然后对回复的数据也进行如上解密,就可以得到命令执行后的对应内容。如此一来,可以得到两个有用有用的信息:
GronKey.txt:
1,50,61,8,9,20,63,41
flag.txt:
TGLBOMSJNSRAJAZDEZXGHSJNZWHG
flag的内容直接提交上去是不对的,因此肯定还需要进行解密,而如何解密就需要用到GronKey.txt,并且按正常思路,GronKey这个名字肯定是个提示。最终搜索到了Gronsfeld密码,解密即可:
from Crypto.Util.number import *from pycipher import Gronsfeldt = [1,50,61,8,9,20,63,41]temp = "TGLBOMSJNSRAJAZDEZXGHSJNZWHG"print (Gronsfeld(t).decipher(temp))
得到:
SICTFSHUMUISAGOODBOYYYYYYYYY
七、fast_morse
题目信息:
你好快啊!(flag需要包含SICTF{})
解题方法:
题目给了一个音频,Audacity打开:

放大后一看就知道是摩斯电码,转换即可
..-. ..--- .- ----- ----. -... ..-. -....- --... ..-. ....- .- -....- ....- ..--- -.... ----. -....- ----. ...-- .- ..... -....- -.-. ---.. .- ....- ---.. ...-- -.... ----- -... ----- ...-- -.-.

在线工具解出来后,换成小写
SICTF{f2a09bf-7f4a-4269-93a5-c8a48360b03c}
八、QR_QR_QR
题目信息:
我就扫码而已啦!为什么要用pwntools?
解题方法:
题目给了一个端口,nc连接:

可以看出是二维码的定位符,那么思路就是把这些0、1转化为二维码并扫码得到数据,复制数据到VScode发现右侧直接出来了视图:

扫码即可

但是上传这串数据的时候发现:

超时了。。。那就需要写脚本进行自动交互,交互一次后发现靶机端还会发送二维码数据,那应该是要循环一定次数后才会给flag了。
exp:
from Crypto.Util.number import *from pwn import *import cv2from PIL import Imagefrom pyzbar.pyzbar import decoder=remote("210.44.151.51",10160)count = 0while(1): count += 1 print(count) data = list(r.recvuntil(b"P")[:-1]) # 定义图像的宽度和高度(根据数据长度调整) width = 116 height = 116 # 创建一个空白图像 image = Image.new("1", (width, height), color=1) # 1表示单色(黑白) # 获取图像的像素访问对象 pixels = image.load() # 将01数据填充到图像中 for y in range(height): for x in range(width): index = y * width + x if index < len(data) and data[index] == 48: pixels[x, y] = 0 # 将0写为黑色像素点 else: pixels[x, y] = 1 # 将0写为黑色像素点 # 保存图像为文件 image.save("1.png") decocdeQR = decode(Image.open("1.png"))[0].data r.sendline(decocdeQR) temp = r.recvline() print(temp) temp = r.recvline() print(temp)
循环1000次后,靶机端发送flag:

SICTF{d7d23552-d917-4ad4-962c-e415dd5b5b6e}
九、问卷调查
题目信息:
本问卷只有认真做的人才能拿到flag呦~(关注公众号并回复sictf领取问卷)
解题方法:
关注公众号按要求来即可,问卷里面就有flag。